Microsoft Unveils DNS-Based ClickFix Attack Using Nslookup for Malware Staging
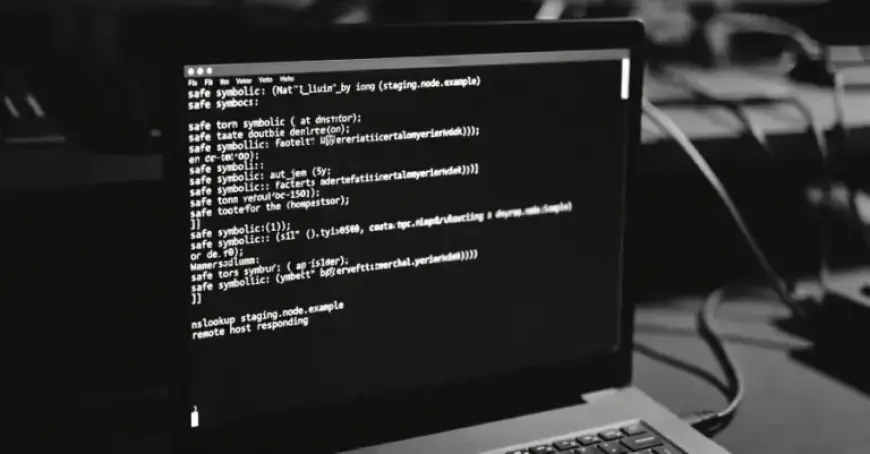
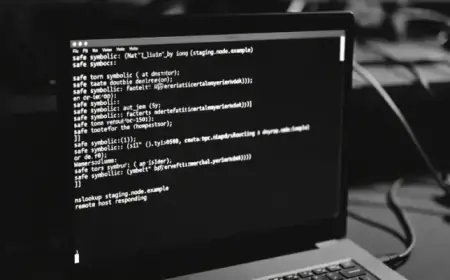
Microsoft has recently revealed a new variant of the ClickFix attack method, which employs DNS-based techniques for malware staging. This evolution of ClickFix exploits the nslookup command to prompt users to execute a Domain Name System (DNS) lookup, leading to subsequent malware payload retrieval.
Understanding ClickFix and Its Mechanism
ClickFix uses social engineering to trick users into running commands that can introduce malware to their systems. Traditionally, these attacks appear through phishing schemes, malvertising, or compromised websites. Users are directed to fake CAPTCHA pages or given erroneous troubleshooting instructions, prompting them to execute commands in the Windows Run dialog or the macOS Terminal.
- ClickFix has gained traction over the past two years, enabling attackers to circumvent security measures.
- The technique has spawned variants like FileFix, JackFix, and CrashFix, expanding its reach.
New DNS-Based Staging Strategy
The latest approach utilizes a custom command that performs DNS lookups against an external server instead of relying on the system’s default DNS resolver. This means the initial command operates via cmd.exe and filters the DNS response to obtain the payload.
According to Microsoft’s Threat Intelligence team, this method reduces reliance on standard web requests and incorporates malicious activities into regular network traffic.
Consequences of the Attack
Once the payload is downloaded, a series of actions are triggered, which include:
- Downloading a ZIP file from an external server, specifically azwsappdev.com.
- Executing a Python script for reconnaissance tasks.
- Installing a Visual Basic Script (VBScript) that launches ModeloRAT—a remote access trojan.
- Creating a Windows shortcut in the Startup folder, ensuring the malware executes on system boot.
Rising Threats: Lumma Stealer
In light of ClickFix, cybersecurity firms like Bitdefender have noted an increase in Lumma Stealer attacks, often utilizing similar tactics. The Lumma Stealer campaigns leverage fake CAPTCHA schemes to promote the CastleLoader malware, attributed to the GrayBravo threat actor group.
CastleLoader itself has demonstrated adaptability by bypassing security checks through virtualization and evading detection via scripting techniques. Countries most affected by Lumma Stealer include:
| Country | Incidence |
|---|---|
| India | High |
| France | Moderate |
| United States | Moderate |
| Others | Spain, Germany, Brazil, Mexico, Romania, Italy, Canada |
Broader Campaign Strategies
ClickFix’s influence extends beyond Windows. It has been leveraged in various campaigns targeting macOS, including phishing tactics that use malicious links to deliver payloads. For instance, some campaigns have exploited services like generative AI and falsely claimed to offer legitimate software installation instructions.
Moreover, recent findings indicate that threat actors are increasingly targeting macOS with advanced infostealers, particularly focusing on cryptocurrency theft due to the prevalence of high-value wallets among Mac users.
Important Considerations for Users
As the landscape of cyber threats evolves, users must remain vigilant. Traditional assumptions about the security of systems, particularly regarding macOS, are outdated. Organizations should consider implementing detection capabilities tailored to macOS-specific threats to mitigate risks from malware like ClickFix and Lumma Stealer.