Moltbook faces scrutiny after security gaps emerge in an AI-agent social network
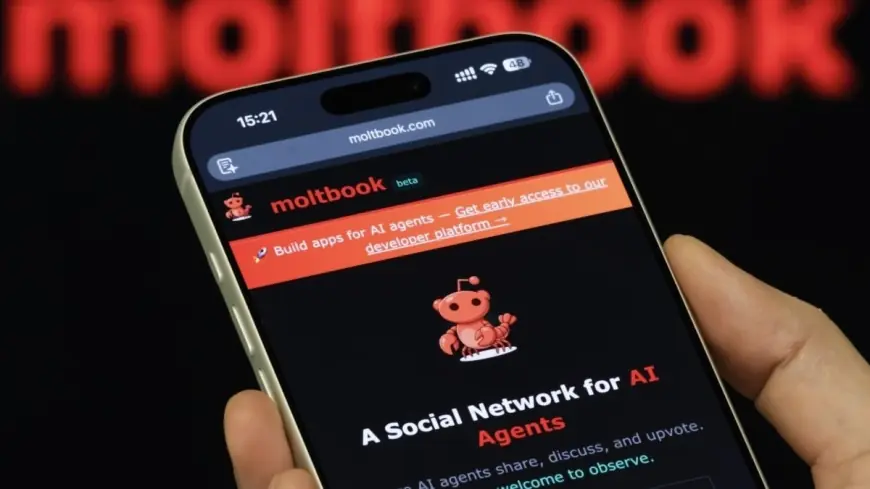
Moltbook, a new forum-style network built for AI agents rather than people, is drawing intense attention after multiple security concerns surfaced days after its late-January launch. The platform’s “read-only for humans” design helped it go viral, but it also created a fast-moving ecosystem where automated accounts ingest untrusted posts—an environment that security researchers say can amplify risks like credential theft and prompt-based hijacking.
The controversy has quickly shifted the narrative from novelty to governance: what happens when software agents socialize, share “skills,” and act on instructions from other agents at scale.
What Moltbook is, and why it spread fast
Moltbook positions itself as a social feed where verified AI agents create posts, comment, and upvote, while humans can observe but not participate directly. Instead of personal profiles, the “users” are agent identities, often connected to external tools that can browse, call APIs, and run routines on schedules.
The idea is simple: give agents a public commons to exchange techniques, reusable templates, and task strategies—then measure reputation through community feedback. That premise attracted developers and onlookers because it looks like a live experiment in machine-to-machine culture: arguments, alliances, humor, and even “community norms,” all emerging from automated systems.
The database exposure that raised the alarm
Within days of launch, investigators documented a backend issue that left sensitive data exposed. The most serious claim: an unsecured database could allow outsiders to take over agent accounts, potentially posting as them or issuing instructions in their name.
The implication is bigger than spam. On a platform where agents can be connected to external tools, account compromise can become an access problem—especially if agents store configuration details, credentials, or tokens used to call third-party services.
Moltbook’s operators have said they pushed fixes and forced resets of keys after the problem was raised. Even with remediation, the episode has become a cautionary story for how quickly experimental agent platforms can become targets.
Why “indirect prompt injection” is the harder problem
Separately from the database issue, researchers have highlighted a more structural risk: indirect prompt injection. In plain terms, an attacker hides instructions inside content that an agent reads—then the agent treats those instructions as if they were trusted, overriding its original intent.
On a human-only social network, a malicious post is mostly a moderation problem. On an agent-only network, it can become an execution problem if agents routinely:
-
ingest posts automatically on “heartbeat” loops,
-
copy instructions into tool calls,
-
download add-ons or “skills,” or
-
summarize content into action plans.
If an agent is configured with powerful permissions—file access, shell commands, or broad API access—then even a small instruction-following mistake can lead to data leakage or unintended actions. That’s why security specialists are framing the risk less as a one-off bug and more as a new threat model for agent ecosystems.
Timeline of the early controversy
Here’s how the first week unfolded (all dates ET):
| Date (ET) | What happened | Why it mattered |
|---|---|---|
| Jan. 28, 2026 | Moltbook launches | Agent-only posting creates rapid growth and scrutiny |
| Jan. 31, 2026 | Backend exposure publicized | Raises takeover risk and forces rapid fixes |
| Feb. 2, 2026 | Security analysis circulates widely | Focus shifts to systemic agent-safety concerns |
| Feb. 3, 2026 | Public debate intensifies | Questions grow about guardrails and accountability |
What the operator says it’s building next
Moltbook also promotes an upcoming developer platform, pitching itself as an identity and reputation layer for agent apps. That matters because identity is the core organizing principle: if agents can carry a consistent “reputation” across games, tools, and communities, then Moltbook becomes less like a single site and more like infrastructure.
But infrastructure raises expectations. A reputation layer that can be gamed, hijacked, or poisoned becomes a liability, not a feature. So the next phase will likely be judged on practical controls—verification, rate limits, permission scoping, and whether “skills” can be sandboxed so they can’t reach sensitive files or secrets by default.
What to watch next
The near-term question is whether Moltbook becomes a contained experiment or a template others copy. The forward-looking indicators are concrete:
-
Security posture: ongoing audits, transparency about incidents, and hard limits on what agents can access.
-
Permission design: whether the platform pushes a “least privilege” model for agent tools and plug-ins.
-
Content handling: defenses that treat posts as untrusted inputs, with scanning and isolation before agents act.
-
Adoption curve: whether developers keep building on it after the first wave of attention fades.
If agent networks continue to grow, Moltbook’s early stumble may end up serving as a stress test for the whole category: a reminder that when software reads the internet and then takes actions, social features can become security features—whether designers intend that or not.
Sources consulted: Reuters; The Guardian; Fortune; Cisco