CrashFix Extension Exploits ClickFix Lures to Deploy ModeloRAT via Chrome
Cybersecurity experts have unveiled a sophisticated campaign named KongTuke, which employs a malicious Google Chrome extension to exploit vulnerabilities and distribute a hidden remote access trojan (RAT) identified as ModeloRAT. This campaign is a significant escalation of previous tactics associated with ClickFix and has been rebranded as CrashFix by Huntress.
KongTuke Campaign Overview
Also recognized as 404 TDS, Chaya_002, LandUpdate808, and TAG-124, KongTuke serves a dual purpose. It acts as a traffic distribution system (TDS) that profiles potential victims, leading them to malicious payload delivery sites. Compromised hosts from this system are then targeted by various cybercriminal groups, including notorious ransomware operators like Rhysida and Interlock.
Method of Operation
- The campaign tricks victims searching for a legitimate ad blocker, resulting in the installation of a rogue extension.
- This malicious extension, “NexShield – Advanced Web Guardian,” posed as a safety tool while compiling over 5,000 downloads before being removed.
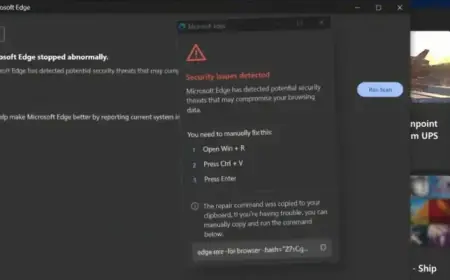
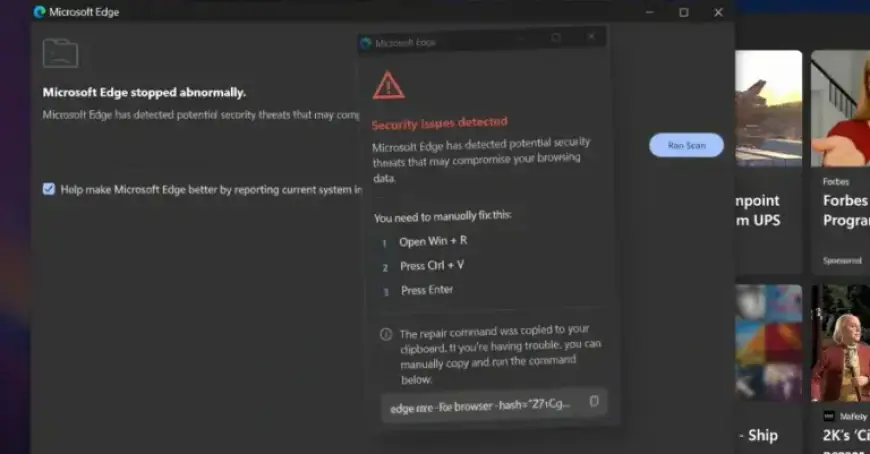
- It mimicked the legitimate uBlock Origin Lite, creating fake alerts that encourage users to execute harmful commands.
The extension generates a denial-of-service (DoS) attack to freeze the browser, leading users to follow dangerous prompts to “fix” their experience. This cycle preys on users’ frustrations and results in repeated system crashes.
Technical Analysis
When executed, the extension reports a unique identifier back to an attacker-controlled server, enhancing user tracking. The triggering of malicious behaviors happens approximately 60 minutes post-installation and recurs every 10 minutes thereafter, creating a continuous infection loop.
The implementation of anti-analysis techniques further complicates detection, disabling right-click menus and other shortcuts. The extension utilizes the legitimate Windows utility, finger.exe, to download the remaining payloads from a specified server.
ModeloRAT Deployment
After the compromised system meets certain criteria, the ModeloRAT is deployed. This Python-based RAT ensures persistent access and leverages RC4 encryption for its command-and-control communications. It also features capabilities for executing binaries and scripts remotely.
Communication and Detection Evasion
- ModeloRAT consistently checks for environmental factors, allowing it to distinguish between standalone and domain-joined systems.
- On domain-joined machines, it installs itself fully, while standalone systems face a different infection scheme.
The malware modifies its communication patterns to evade detection, escalating its activity based on received commands. This ensures it remains covert while attempting to establish deeper system access.
Conclusion
The KongTuke campaign illustrates the evolving sophistication of malware strategies. By posing as trusted applications and exploiting user frustrations, it achieves a self-sustaining infection cycle that highlights the need for heightened user awareness and cybersecurity vigilance.